Cyber Threats Are Evolving. Are You Ready?
Cybercrime is at an all-time high, and no business is safe. Every 39 seconds, hackers launch new attacks, targeting companies of all sizes. Ransomware, phishing, and data breaches can cripple your operations, cost millions in damages, and destroy your reputation..
If your business isn’t secured, it’s only a matter of time before you’re next.
At Sautech, we provide AI-powered cybersecurity solutions that detect and stop cyber threats before they destroy your business. We’re an authorized SentinelOne and CheckPoint partner, offering enterprise-grade protection, penetration testing, and managed security services.
Why Businesses Trust Sautech for Cybersecurity:
SentinelOne: Autonomous AI-Driven Cybersecurity

SentinelOne is a cutting-edge, AI-powered cybersecurity platform that provides enterprise-wide protection against ever-evolving cyber threats.
As a SentinelOne Authorized Partner, Sautech offers a cloud-managed solution that ensures your devices are continuously monitored and protected in real time.
This enterprise cybersecurity software eliminates the need for traditional, human-powered systems by leveraging advanced AI to detect and respond to cyber threats autonomously. Whether you are a small business or a large enterprise, SentinelOne offers the visibility, control, and protection your organization needs.
Key Benefits of SentinelOne:
At Sautech, we integrate SentinelOne into your infrastructure, ensuring continuous protection across all devices, helping your business stay one step ahead of cybercriminals.
CheckPoint Firewall: Advanced Threat Prevention
CheckPoint Firewall is one of the most trusted names in cybersecurity, offering advanced threat prevention and simplified management. Our security gateways integrate multiple technologies to safeguard your network, providing a robust defense against cyberattacks while minimizing complexity and reducing costs.

Key Features of CheckPoint Firewall:
We offer CheckPoint Firewall in three flexible service models:
Device Support: Ongoing support for your firewall devices to ensure they remain secure.
Licensing: Access to the latest firewall security software and updates.
Managed Services and Outsourced Support: Let us manage and monitor your security environment so you can focus on your business operations.
Whether deployed on branch devices or hosted in data center instances, CheckPoint Firewall is a critical component of a secure IT infrastructure.
Server & Infrastructure Optimization

Effective server and infrastructure optimization is essential for ensuring that your IT systems perform at their best. Sautech specializes in enhancing your server hardware, software, and network infrastructure to improve performance, reduce downtime, and optimize resource utilization.
Optimization Services Include:
By continuously monitoring server performance and implementing industry best practices, Sautech helps businesses maximize system reliability, scalability, and cost-efficiency. Our managed backup solutions ensure that your data is always protected, even in the event of an unexpected failure.
Penetration Testing
Penetration testing (also known as ethical hacking) is a proactive cybersecurity measure that simulates real-world cyberattacks to uncover vulnerabilities in your systems. Sautech’s penetration testing services help identify weaknesses before malicious actors can exploit them, strengthening your organization’s defenses.
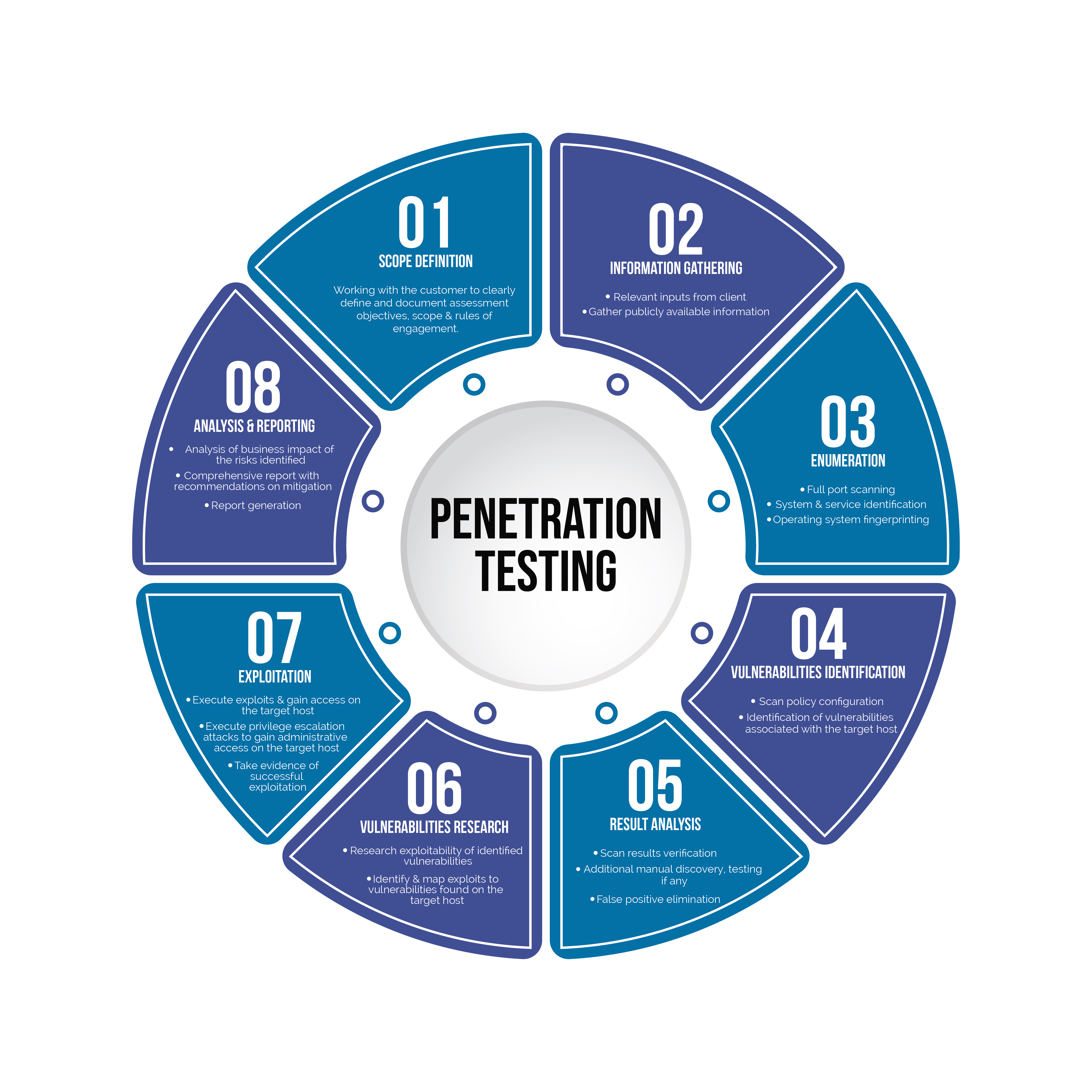
Our Penetration Testing Process:
With extensive experience in conducting penetration tests across Southern Africa, Sautech ensures that your IT infrastructure remains secure and resilient. Our detailed reports, often used by insurance companies and IT providers, include a "how-to" guide for addressing identified vulnerabilities and implementing effective security measures.
Ethical Hacking (White Hat)
Ethical hacking involves using the same techniques as cybercriminals to simulate cyberattacks on your systems. By conducting ethical hacking, Sautech identifies and addresses vulnerabilities proactively, ensuring that your business stays ahead of potential threats.

Key Services of Ethical Hacking:
By identifying vulnerabilities and offering remediation plans, Sautech helps organizations stay secure against both external and internal threats. Ethical hacking is a crucial component of any comprehensive cybersecurity strategy.
Why Choose Sautech for Your Cybersecurity Needs?
At Sautech, we are committed to providing top-tier cybersecurity services that meet the unique needs of businesses in Southern Africa. Our team of certified cybersecurity experts uses the latest technologies and methodologies to keep your business safe from evolving cyber threats.
Our Key Differentiators:
Secure your business today with Sautech’s enterprise cybersecurity solutions. Contact us to learn more about our services or get a free consultation on how we can help protect your digital assets.


